Pluggable Authentication Modules for Linux, Security, by Andrew G, Morgan, on December 1, 1997 , Have you ever wondered how much work it would be to modify login to work the way you want it to? Perhaps you want it to refer to shadowed passwords or you don’t want to let users log in during certain times of the day, Perhaps your policy is to ensure that root cannot log in anywhere …
Linux PAM
Overview
Anatomy of a Linux Pluggable Authentication Modules PAM
linux pluggable authentication modules
Pluggable authentication modules are a common framework for authentication and security Both of Red Hat Enterprise Linux’s single sign-on methods — Kerberos and smart cards — depend on underlying PAM configuration Understanding and using PAM can be very beneficial for planning and implementing a secure, efficient single sign-on solution,
In Red Hat Enterprise Linux many programs are configured to use a centralized authentication mechanism called Pluggable Authentication Modules PAM PAM uses a pluggable modular architecture which affords the system administrator a great deal of flexibility in setting authentication policies for the system, In most situations, the default PAM configuration file for a PAM-aware …
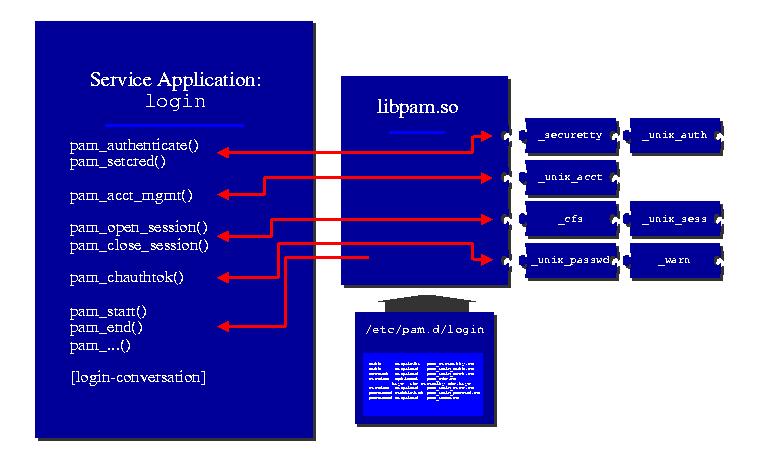
An introduction to Pluggable Authentication Modules PAM
In a previous article I described the flow of an application calling PAM libraries for authentication at a very high level In this article we will walk through the configuration files for a local sudo command, When using sudo we switch users and do somethingThis privilege change requires verification that we are who we say we are and are allowed to perform the given action,
Chapter 2 Using Pluggable Authentication Modules PAM
Pluggable Authentication Modules PAM have been around since 1997 I was taught that PAM originated from Sun’s Solaris and it does appear that the first enterprise use and popularization occurred there However according to a 1997 article I found the first full implementation was the Linux-PAM deployment The article is still available from
424 Pluggable Authentication Modules PAM
Linux-PAM short for Pluggable Authentication Modules which evolved from the Unix-PAM architecture is a powerful suite of shared libraries used to dynamically authenticate a user to applications or services in a Linux system, It integrates multiple low-level authentication modules into a high-level API that provides dynamic authentication support for applications, This allows …
Pluggable Authentication Modules — Wikipédia
Vue d’ensemble
Pluggable authentication modules UNIX or Linux
Pluggable Authentication Modules PAM
Linux
Linux-PAM This is the primary distribution site for the Linux-PAM Pluggable Authentication Modules for Linux project Things to be found here are documentation and source code for Linux-PAM Documentation Online documentation; Offline documentation; Red Hat run the mailing list for this project To look at the archives subscribe or unsubscribe from the list look here: the PAM mailing list
Pluggable authentication modules UNIX or Linux A Pluggable Authentication Module PAM is a well-defined framework for supporting different authentication modules that were originally developed by Sun Microsystems PAM is supported in both 32- and 64-bit modes on Solaris Linux HP-UX and AIX®, System administrators can use PAM to implement
Pluggable Authentication Modules for Linux
This lecture is part of my full course on LFCS which is located herehttps://www,udemy,com/course/red-hat-certified-engineer-rhce/?referralCode=17A25B4023C262
A Linux-PAM page
Pluggable Authentication Modules, Linux – Umask user mask SSH – OpenSSH Server sshd Linux – Environment variable, Linux – /etc/passwd public user information Linux – /etc/shadow Secure user information Postfix – Authentication configuration SASL for a connection to the SMTP server 587 Email – on Linux,
How to Configure and Use PAM in Linux
Linux Pluggable Authentication Modules PAM
Cliquez pour afficher sur Bing33:13
Pluggable Authentication Modules PAM permet de contrôler les authentifications et les autorisations sur un système Linux de manière unifiée et avancée grâce à des stratégies et à des modules, Nous verrons dans ce chapitre comment paramétrer PAM pour des applications et comment créer un nouveau module,